Basics
I2P’s aim is to create an anonymous network which offers a simple network layer for applications of many kinds.
Every user of I2P routes traffic for other users. All the traffic is encrypted a few times. So all the stuff that users forward is only usable for the sender and the final destination. You are not responsible for what you route.
I2P doesn’t hide the fact that you run I2P. It even publishes your IP in the NetDB. Any service that is offered by your router has a own destination (~I2P-IP). There is not any relation between a public destination key and a IP address: You are anonymous, in technical terms.
Offcourse this comes with some drawbacks. I2P is not so fast than the plain internet. Every packet must be routed over a certain count of other I2P-participants.
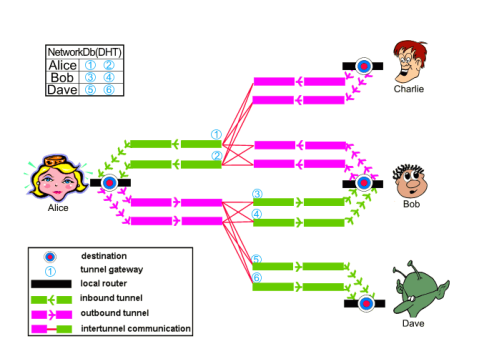
This graphic shows the work that is done behind the scenes of I2P in a very simplyfied way
You can never be 100% anonymous but I2P tries to come as close as possible to that.
Jo said
Looks nice, but why should I use this instead of TOR?
i2plog said
I will create a page later about the differences between and advantages/disadvantages of I2P and TOR.
I list only a few of them:
TOR is designed to have many users that “leech” only and a few outproxys to the net.
I2P was not primary designed to surf the real internet, it was designed to create a “darknet” (invisible internet project). there are some outproxys within i2p but they are not safe (passwords can easily be sniffed). and everybody is “leecher” and “seeder” (share your bandwith with others)
TOR is made primary for surfing and chatting whereas I2P can transport almost everything (chat, http, bittorrent)
BTW: you can even run filesharing over I2P (but e.g. only torrents of i2p-internal trackers will work)
i2plog said
for a more detailed and more technical view on that:
http://www.i2p2.de/techintro.html#similar.tor